Breaking
Atlantic Superstore customers might be affected by hack
Loblaw is advising all users to change their passwords

caption
The view outside the Atlantic Superstore on Quinpool.
caption
The view outside the Atlantic Superstore on Quinpool.The latest in major online security breakdown will have Nova Scotians checking their wallets.
The Loblaw Corporation went on record this week to say there was a breach of their systems. According to a statement by Kevin Groh, the company’s vice-president of corporate affairs and communication, “Individual member accounts were accessed and points were stolen.”
This potentially affects all Nova Scotia customers who collect reward points at Atlantic Superstore locations, or who utilize any portion of the PC Financial services, along with all other grocery stores that use the PC Plus system, like Loblaws, in Ontario.
The website manages credit cards under the PC Financial label as well, but there have been no reports of those cards being misused.
Not long before the breach was announced, users of the site received an email on Jan. 25 urging them to change their passwords. It mentioned recent account information leaks on Yahoo! and LinkedIn and advised users who use the same passwords on multiple websites to create unique passwords. It also said PC Plus had not been affected by a security breach.
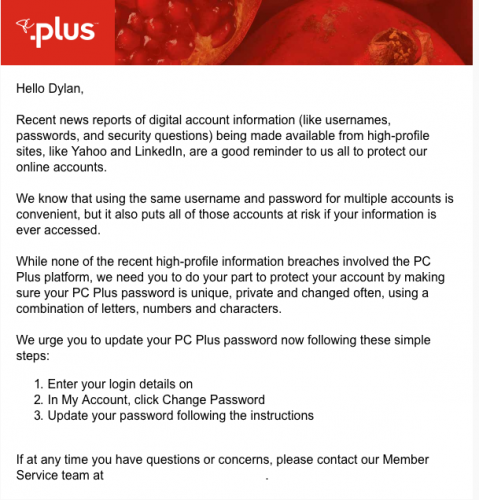
caption
The email that was sent out to PC Plus users January.Loblaws did not respond by press time to a request for comment on whether they had noticed any suspicious activity at the time of the email.
Steven Bellovin is a professor of computer science at Columbia University. Quoting a supposed phrase by ’50’s bank robber Willie Sutton, he says these kinds of attacks are becoming more frequent “because that’s where the money is.”
“We’re seeing more attacks on online services because they now represent value, in a way they did not 10 to 15 years ago,” he adds. On top of that, he says that “many places do security wrong and you have a recipe for trouble.”
Anil Somayaji, a professor of computer science at Carleton University and expert in the field of computer security, has noticed these attacks ramping up as well.
“People seem to be kind of getting used to these things because security systems are Swiss cheese,” says Somayaji. “It turns out that breaking into them isn’t that hard for anyone who really wants to.”
Frank Breitinger, a computer science professor at the University of West Haven, says it’s hard to keep up with all of the security breaches.
“I think we need laws that enforce the notification of users (when their information is compromised),” he says. “Companies try to keep them secret as it is bad publicity.”
He suggests a centralized platform for reporting all new hacks that are discovered.
Paul Haven, head of the cybersecurity program offered at Webster University, says while the media does a good job getting the word out when a hack occurs, there’s more work to be done.
Particularly, he emphasizes the difference between “white-hat” hackers in it for the fun or challenge,and “black-hat” hackers looking to cause harm.
“Companies need to hire the white-hats to test their systems for vulnerabilities,” he says.
Is a strong password enough?
Many websites today encourage or require users to create what they call a “strong” password, as well as to have a unique password for every account.
Bellovin says advising users to pick a strong password is “one of the worst pieces of security advice out there.”
He says these complex passwords are hard to memorize. That leads people to reuse passwords on multiple sites — which means if a hacker gets one password, they get them all.
Somayaji says that strong passwords for each account are useful, but adds “there’s no way you can remember them all.”
He points to password managers as a solution to this problem.
Two-factor authentication is another way to increase security, Somayaji says. That’s a security measure which requires a code sent to the user’s phone via text or app to be entered alongside or instead of a password.
“It’s not perfect,” he says. “It’s possible to breach accounts with two-factor authentication, but it’s much harder.”
The human factor
Even if systems improve on the technical side, people will still make mistakes, says Somayaji.
“The problem is these systems have to be used by people,” he says. “Just as a con artist has ways of exploiting people’s trust, there are ways of fooling people in the loop and computers in the loop.”
He says the practice of deception to trick people into giving out sensitive information is one of the biggest holes in every security plan. For example, he says, a hacker could call up a company pretending to be an employee’s friend or relative and say they need access because the person they’re pretending to know is sick.
If someone really wants to break into your account, they probably will, he says.
Haven says businesses can get away with letting these major breaches happen, so long as it doesn’t cut into their profits.
“If we show the companies that we’ll stop being a customer unless they improve their security, they’ll start to listen,” he says.

